
Cloud solution has been a trending boardroom topic amongst leadership in Southeast Asia long before COVID-19. Now with business continuity and remote working become the agenda to survive the pandemic, many have accelerated their cloud adoption and migration strategy. These proactive approaches to transform digitally can be witnessed across legacy enterprises from manufacturing to logistics.
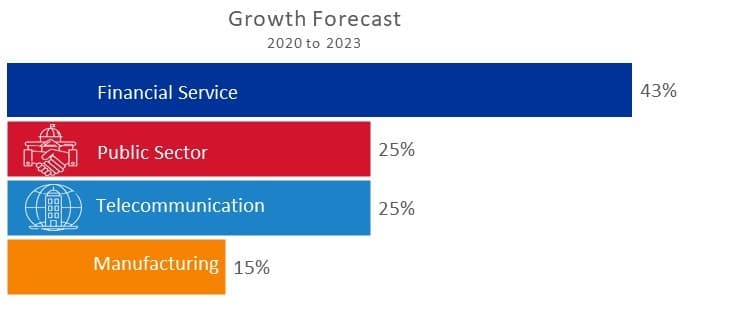
Southeast Asian Governments, Malaysia included, are shifting to a more favourable stance on cloud by amending national policies, creating frameworks and launching digital transformation (DX) initiatives. The Malaysia Digital Economy Blueprint, MyDIGITAL, for instance, is Malaysia’s national response to drive digitalisation amongst businesses and government agencies while bridging the digital divide across the country. To realise this ambition, in the first phase of the blueprint (2021-2022), the Government aims to move towards a paperless environment and migrate 80% of public data to hybrid Cloud systems by the end of 2022, but why?
Although Cloud is well spoken of, the concept of how it is imperative to digital transformation remains vague to many. Hence, to understand its synonymity, it is important to debunk the technology.
Foremost, the technology can be differentiated into three (3) models:
Top three (3) advantages:
Top three (3) advantages:
Top three (3) advantages:
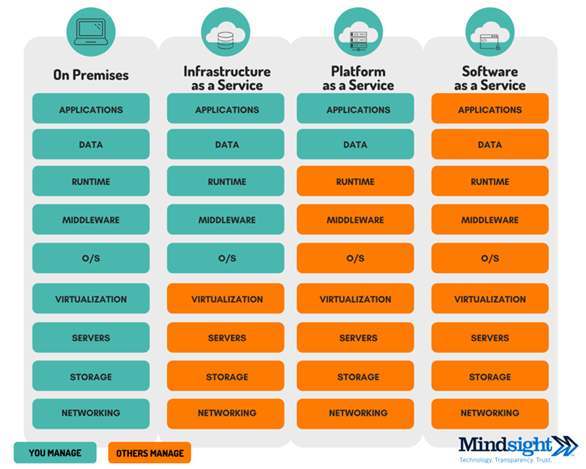
Within each model, Cloud is further defined by its service types with differing level of responsibilities between the user and service providers.
Unlike traditional infrastructure, the flexibility, accessibility and scalability of Cloud prepare enterprises and governments to stand resilient against any given circumstances and allow them to act quickly to ensure competitive advantage in the market.
All enterprises, across industries and sizes, experience data loss caused by unintentional events such as system failures and natural disasters. While there are methods to prevent data-loss events, the most effective data-protection method is having an enterprise-wide backup solution.
However, with the exponential growth of data worldwide, backup solutions are required to be comprehensive. Traditional backup methods such as tape libraries are unable to quickly scale to this growth and maintaining them can be extremely cost-intensive.
Thus, a growing number of organisations are moving on-premises backup capabilities to the Cloud in order to accommodate this data growth. Some of the benefits include:
In today’s data-driven environment, enterprises are required to overcome data silo challenges and find efficient and innovative ways to uncover hidden insights within their data to remain competitive. However, to build constantly evolving capabilities in-house is no easy task, hence leading digital companies e.g. Netflix, or regional favourites e.g. Grab, look towards Cloud providers and their partners for such solutions. They provide real-time analytics, big data processing and more which enable enterprises to streamline its business intelligence process of gathering, integrating and presenting insights to enhance business decision making.
What are the values for enterprises?
In Southeast Asia, more and more enterprises are using Cloud for innovation projects. Those that do not look lean on Cloud for R&D, seem to lack behind their counterparts who do. This is simply because upfront technology investment into on-premise infrastructure is heavy and procurement periods are long, barring them from constant innovation to address consumer needs. On the contrary, Cloud is readily available, can be scaled down or up, and is armed with various tools and software to support innovation. Thus in terms of cost, timeframe and manpower, Cloud is an indisputable option for R&D.
One of the biggest challenges for Cloud adoption in Southeast Asia remains to be the talent crunch. This challenge is extremely prevalent in Indonesia as they house only about 75,000 IT engineers in the country, while they require at least 10x the number to fully sustain a digital economy.
Furthermore, digital talent often aims to work in digital companies, which impedes the digital journey of legacy enterprises. Hence, Cloud service providers play a vital role in the region as they have the people, experience and capability and they provide end-to-end support to ensure true Cloud optimisation.